DKIM Records Explained
DomainKeys Identified Mail (DKIM) is an authentication standard used to prevent email spoofing. Specifically, DKIM attempts to prevent the spoofing of a domain that's used to deliver email.
DKIM employs the concept of a domain owner who controls the DNS records for a domain. When sending email with DKIM enabled, the sending server signs the messages with a private key. A domain owner also adds a DKIM record, which is a modified TXT record, to the DNS records on sending domain. This TXT record will contain a public key that's used by receiving mail servers to verify a message's signature. The DKIM public-key cryptography process allows recipients to be confident of a sender's authenticity.
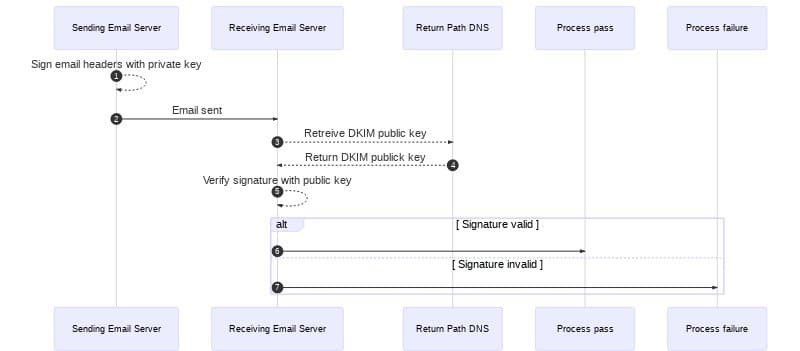
To understand DKIM, it may be helpful to understand how email is sent when DKIM is added to the process. Imagine an email sent by sender@example.com. For DKIM to work properly, the following steps take place:
- Before sending the message, the sending server signs the email using a private key.
- When the message is delivered, the receiving server obtains the DKIM record from the DNS records for
example.com. - The receiving server then uses the public key in the DKIM record to verify the message's signature.
- If the DKIM check passes, the receiving server can be confident the message was sent by the address in the
return-pathand wasn't altered in transit. - If the DKIM check fails, the message is likely illegitimate and will be processed using the receiving server's failure process.
While DKIM authentication is an email best practice, it's important to understand that a DKIM signature is limited in scope. It does not verify content or tell the receiver to treat the message any differently. Its main purpose is to help verify Sender Identity, which is an important factor (although not the only factor) when it comes to email delivery.
You can authenticate with DKIM yourself, or the DKIM signature can be created by your sending message transfer agent (MTA). Setting up DKIM can be a complex process. If not done right, Internet service providers (ISPs) will block your email, particularly because incorrect implementation is a sign of a spammer.
SendGrid automatically enables DKIM for all email to improve your email deliverability, whether you're on a shared IP or a dedicated one. This is just one more example of how SendGrid helps thousands of customers follow email best practices to ensure maximum delivery for their emails.
When you set up an authenticated domain, you will be given the option of using automated or manual security. When you select automated security, SendGrid will manage your DKIM and SPF records for you. This means that whenever you make a change to your account that could impact your deliverability, such as adding a new dedicated sending IP address, SendGrid will automatically update your DNS settings and your DKIM signature.
Multiple selectors ("s1" and "s2", by default) are used interchangeably and rotated when necessary. Only one selector is active and used for signing DKIM at any given time.
Info
SendGrid will always provide you with a custom DKIM signature. However, your custom DKIM signature is only automatically updated if you select automated security when authenticating your domain. If you turn automated security OFF, you will be responsible for updating your DKIM signature whenever you make a change to your sending domain.
1subdomain.example.com. | CNAME | uXXXXXXX.wlXXX.sendgrid.net2s1._domainkey.example.com. | CNAME | s1.domainkey.uXXX.wlXXX.sendgrid.net.3s2._domainkey.example.com. | CNAME | s2.domainkey.uXXX.wlXXX.sendgrid.net.
1em1234.example.com | MX | mx.sendgrid.net2em1234.example.com | TXT | v=spf1 include:sendgrid.net ~all3m1._example.com | TXT | k=rsa; t=s; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDPtW5iwpXVPiH5FzJ7Nrl8USzuY9zqqzjE0D1r04xDN6qwziDnmgcFNNfMewVKN2D1O+2J9N14hRprzByFwfQW76yojh54Xu3uSbQ3JP0A7k8o8GutRF8zbFUA8n0ZH2y0cIEjMliXY4W4LwPA7m4q0ObmvSjhd63O9d8z1XkUBwIDAQAB
When it comes to email security and authenticity, DomainKeys Identified Mail (DKIM) plays a pivotal role. DKIM is an authentication standard designed to prevent email spoofing and bolster the trustworthiness of email communications.
DKIM revolves around the concept of a domain owner who has control over the DNS records for a particular domain. To enable DKIM, the sending server signs outgoing messages using a private key. Simultaneously, the domain owner adds a DKIM record to the DNS records of the sending domain. This DKIM record, essentially a modified TXT record, contains a public key. Receiving mail servers leverage this public key to verify the authenticity of a message's signature. In essence, DKIM public-key cryptography assures recipients of the sender's legitimacy.
To grasp how DKIM operates, consider the email flow with DKIM in action. Suppose sender@example.com sends an email:
- Signing with a Private Key: Before dispatching the message, the sending server signs it using a private key.
- Retrieving DKIM Record: The receiving server fetches the DKIM record from the DNS records associated with example.com.
- Verifying the Signature: Utilizing the public key from the DKIM record, the receiving server verifies the email's signature.
- Successful DKIM Check: If the DKIM check passes, the receiving server can confidently attribute the email to the sender in the return-path and ensure it wasn't tampered with during transit.
- Failed DKIM Check: In the event of a failed DKIM check, the email is likely considered illegitimate and subject to the receiving server's anti-spam measures.
While DKIM authentication is a vital email best practice, it's important to note its scope. DKIM doesn't assess email content or instruct receivers on how to handle messages differently. Its primary purpose is to establish Sender Identity, a crucial factor in email delivery, although not the sole determinant.
Configuring DKIM can be intricate, and any missteps may lead to email blocking by Internet service providers (ISPs), as improper implementation is often associated with spammers.
SendGrid simplifies DKIM configuration by automatically enabling it for all email, promoting enhanced email deliverability whether you're on a shared or dedicated IP address. This exemplifies SendGrid's commitment to helping customers adhere to email best practices and maximize their email delivery rates.
Moreover, when you set up an authenticated domain, you have the option of choosing automated or manual security for your DKIM and SPF records. Opting for automated security empowers SendGrid to handle updates to your DNS settings and DKIM signature whenever you make changes that impact deliverability, such as adding a new dedicated sending IP address. If you prefer manual control, you'll be responsible for DKIM signature updates when modifying your sending domain.
Save time and feel confident you are set up for long-term success with Email Implementation. Our experts will work as an extension of your team to ensure your email program is correctly set up and delivering value for your business.