Networking Considerations for Video Applications
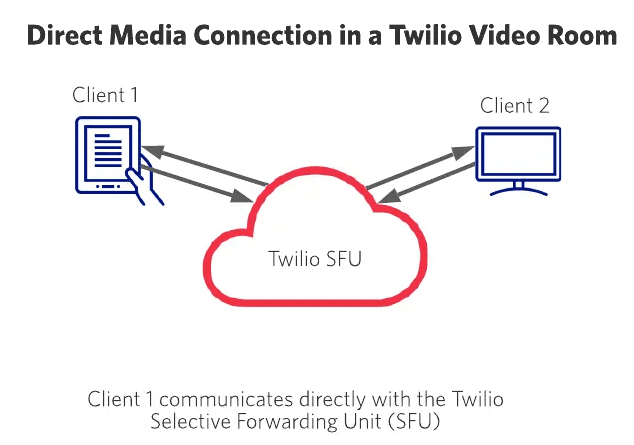
In real-time video applications, clients must be able to exchange audio, video, and other media with one another with the lowest possible latency. When clients connect to a video Room, the Twilio Video SDK tries to establish a direct media connection between the client and Twilio's media server (also called a Selective Forwarding Unit, or SFU).
Firewalls and Network Address Translation (NAT) can impact the quality and performance of your application if they block direct communication of media.
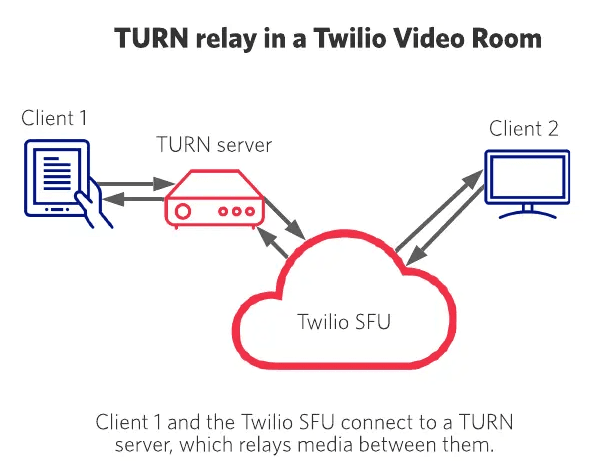
If a direct connection cannot be established between a client and Twilio's media servers, Twilio uses a TURN relay to exchange media. Using TURN adds additional latency to the application, as it adds an extra hop between the client sending the media and the client receiving the media.
Common reasons why a direct connection could fail are firewalls that restrict UDP traffic on Twilio's specified ports or non-BEHAVE-compliant NATs, which can't be traversed using standardized methods.
What is a BEHAVE-compliant NAT?
Below are the protocols and ports through which Twilio will attempt to establish a connection for media exchange, in order of preference. Using TURN-TLS on port 443 adds the highest amount of latency to the transmission of media, because in addition to requiring a TURN relay, it adds in delivery acknowledgments and packet retransmission. It is a last fallback if other communication methods are blocked.
Info
You can also see the IP addresses that Twilio uses to communicate.
| Protocol | Port Range |
|---|---|
| STUN and UDP/TLS/RTP/SAVPF | 10000 - 60000 |
| STUN, TURN-UDP | 3478 |
| TURN-TLS | 443 |
When Participants connect to a Room, Twilio's media server dynamically assigns ports for UDP communication. If direct connectivity checks fail on the assigned ports, then TURN-UDP on port 3478 and TURN-TLS on port 443 are used as fallbacks.
The scenarios below describe situations where a client, Alice, connects to a Room and exchanges media with Twilio's media servers under different network environments.
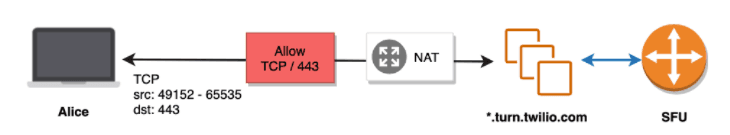
In a non-restrictive network environment or a restricted environment where UDP ports 10000 - 60000 are allowlisted, Alice can establish a direct media connection with the Twilio media server using the specified UDP port range. This is optimal for latency.
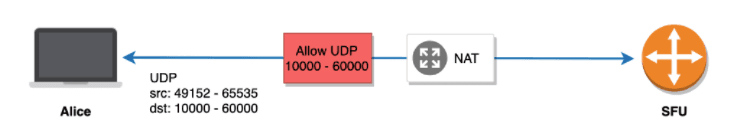
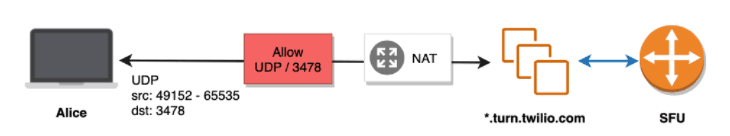
In an environment where only UDP port 3478 is allowed, Alice must relay media through a TURN server in order to connect with the Twilio SFU. This adds marginal latency (< 50ms) because the TURN server is now relaying media between Alice and the Twilio media server, rather than Alice directly communicating with the media server.
In an environment where only TCP/TLS port 443 is allowed, the client must relay through the TURN server in order to connect with the SFU. This adds higher latency (> 50ms) because the TURN server is now relaying media using TCP/TLS between the client and the media server. TCP/TLS adds delivery acknowledgments and retransmission, which can further delay transmission of real-time media.