Verify TOTP Overview
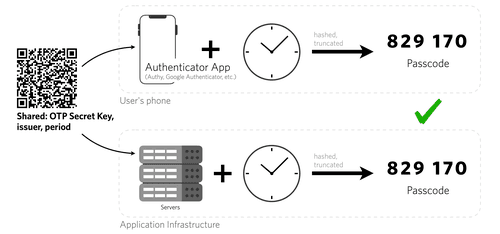
Time-based one-time passcode (TOTP) is a strong authentication choice for users who can download a special app like Authy or Google Authenticator on their mobile device or computer. These authenticator apps generate unique numeric tokens with a standardized algorithm that uses the current time as an input. Some benefits of TOTP include:
- More security: Tokens automatically expire and there are no one-time passwords (OTPs) for fraudsters to intercept, making it more secure than SMS, email, or voice channels.
- Works offline: Generating and verifying a TOTP token does not require internet connectivity as long as a device's time is synced.
- No PII required: TOTP does not need a phone number to work, so no personally identifiable information (PII) is stored.
TOTP is a great choice for businesses looking for a more secure, private, and lower-cost user authentication option.
- Technical overview
- Quickstart
- Quick deploy a sample TOTP application
- How to build TOTP support with the Verify API and Google Authenticator
A user is represented as an Entity within Verify TOTP. We advise using an immutable user identifier such as a system UUID, GUID, or SID for the identity property of an Entity so that no PII is stored. See Entity API for more details.
You can fetch an Entity by its identity property, but the control and storage of the identity relation with the user must be managed on your end.
The Factor API also does not store any kind of user information or PII.
If a user has multiple TOTP factors on the same device, ensure that the factorSid of the intended factor is given when using the Challenge API to create a Verification Attempt.
As a best practice, we advise only allowing one TOTP factor (seed) per user at a time. When a user requests to generate a new seed, the old one should be deleted.
See this support article for more information on how to update the logo displayed in the Authy App for your TOTP.