Verify TOTP Quickstart
Info
Want to see this in action first? Check out Twilio's Code Exchange and quick deploy a sample TOTP application.
Info
Looking for open source native libraries that generate TOTPs? Try Kotlin One-Time Password Library for Android or SwiftOTP for iOS.
Verify TOTP adds the standards-compliant TOTP (Soft Token) channel to the Verify API, so that you can let your users use authenticator apps like Authy, Google Authenticator, or your own custom app for authentication. It's great for businesses looking for a more secure, private, and lower-cost user authentication option compared to SMS OTP. TOTP even works when the user is offline, like on an airplane. Unlike the Authy API TOTP feature, no PII from the user is required, more user registration options beyond QR codes are supported, and you can configure more code properties.
There are three main steps to use Verify TOTP:
- Register a user by generating an RFC-6238 compliant seed.
- Verify that the user correctly added the seed (for example via QR code) to their Authenticator App
- To verify a registered user, check that the code a user provided matches the code generated by the unique seed.
This Quickstart will walk you through the entire process step-by-step, starting with setting up your Twilio account all the way through verifying a user.
In this Quickstart, you will learn how to:
- Setup
- Sign up for Twilio
- Create a Verify Service
- Register a user and TOTP seed
- Generate a TOTP seed
- Generate a QR code
- Verify a successful registration
- Verify a user
- Create a Challenge
- Update the Challenge
By the end of this Quickstart, you'll have a solid foundation for implementing Verify TOTP within your app and backend to verify users at login, transaction, and other sensitive actions.
Check out the Verify TOTP Technical Overview to view its data model and sequence diagrams
Info
Already have a Twilio account? Go ahead and skip this section.
You can sign up for a free Twilio trial account here.
- When you sign up, you'll be asked to verify your personal phone number. This helps Twilio verify your identity.
- Once you verify your number, you'll be asked to create a project. For the sake of this tutorial, you can click on the "Learn and Explore" template. Give your project a name, or just click "skip remaining steps" to continue with the default.
- Once you get through the project creation flow, you'll arrive at your project dashboard in the Twilio Console. This is where you'll be able to access your Account SID, an authentication token, create a Verify Service and more.
Go to Twilio Console > Verify > Services and create a new Service.
Alternatively, you can select any existing Service. However, we recommend creating a new service for testing so you don't accidentally interfere with a production environment.
To use Verify TOTP, you first register a user by generating an RFC-6238 compliant seed. Then you verify that they've correctly added it to their Authenticator App for generating codes.
The security of TOTP relies on a shared secret between your app and your user, and this is known as the seed. Register a user by creating a TOTP factor, which generates a seed based on a set of default configs and stores it. A corresponding Entity representing your user is also auto-created if it didn't exist.
For security reasons, it is not possible to export TOTP seeds programmatically after creation and they are not returned from the Factor API. If you do need to save seeds, we recommend performing that operation during seed creation.
When creating a TOTP factor, you can optionally pass your own seed (useful for migration scenarios) and modify the default configs. See the Factor resource for reference. Some default configs are also adjustable at the Service resource level, such that all future Factors use them. Type or paste the code sample for this step.
1// Download the helper library from https://www.twilio.com/docs/node/install2const twilio = require("twilio"); // Or, for ESM: import twilio from "twilio";34// Find your Account SID and Auth Token at twilio.com/console5// and set the environment variables. See http://twil.io/secure6const accountSid = process.env.TWILIO_ACCOUNT_SID;7const authToken = process.env.TWILIO_AUTH_TOKEN;8const client = twilio(accountSid, authToken);910async function createNewFactor() {11const newFactor = await client.verify.v212.services("VAaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa")13.entities("ff483d1ff591898a9942916050d2ca3f")14.newFactors.create({15factorType: "totp",16friendlyName: "Taylor's Account Name",17});1819console.log(newFactor.binding);20}2122createNewFactor();
Response
1{2"sid": "YFaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa",3"account_sid": "ACaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa",4"service_sid": "VAaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa",5"entity_sid": "YEaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa",6"identity": "ff483d1ff591898a9942916050d2ca3f",7"binding": {8"secret": "GEZDGNBVGY3TQOJQGEZDGNBVGY3TQOJQ",9"uri": "otpauth://totp/test-issuer:John%E2%80%99s%20Account%20Name?secret=GEZDGNBVGY3TQOJQGEZDGNBVGY3TQOJQ&issuer=test-issuer&algorithm=SHA1&digits=6&period=30"10},11"options": null,12"date_created": "2015-07-30T20:00:00Z",13"date_updated": "2015-07-30T20:00:00Z",14"friendly_name": "Taylor's Account Name",15"status": "unverified",16"factor_type": "totp",17"config": {18"alg": "sha1",19"skew": 1,20"code_length": 6,21"time_step": 3022},23"metadata": null,24"url": "https://verify.twilio.com/v2/Services/VAaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa/Entities/ff483d1ff591898a9942916050d2ca3f/Factors/YFaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa"25}
Warning
Do not use Personally Identifiable Information for identity. Use an immutable user identifier like a UUID, GUID, or SID.
Verify TOTP uses identity as a unique identifier of a user. You should not use directly identifying information (aka personally identifiable information or PII) like a person's name, home address, email or phone number, etc., as identity because the systems that will process this attribute assume it is not directly identifying information.
Warning
Use caution when changing default configs
The default configs for the TOTP code (Config.CodeLength, Config.Skew, Config.TimeStep, and Config.Alg) have been chosen for a typical TOTP use case with a 6-digit length code. Please use caution when changing these configs, as it could reduce the security of the code. For example, reducing the length of the TOTP code (Config.CodeLength) makes the code easier to guess and more vulnerable to a brute force attack. While a shorter length may be necessary for your use case, consider compensating security enhancements, such as limiting the rate at which codes can be checked, reducing Config.Skew, and reducing Config.TimeStep.
The Authy app will not be able to add TOTP tokens if default configs such as Config.CodeLength or Config.TimeStep are changed. Other publicly available authenticator apps that your users might have don't support non-default configs for all mobile operating systems; see this 3rd-party analysis of authenticator apps for details.
Contact Twilio for further guidance.
The user needs to add the seed, and optionally metadata like Issuer and Account Name, to an authenticator app like Google Authenticator, Twilio Authy, or a custom client app that you've provided to your user. This authenticator app needs to securely store the seed and generate TOTP codes using it. A typical way for the user to add the seed is via scanning a QR code. Verify TOTP generates a standard URI (factor.binding.uri) that you can convert into a QR code for this purpose. Verify TOTP does not generate the QR code itself, but there are many free/open-source QR code generators.
For this quickstart, use qr-code-generator.com to quickly generate a QR code by pasting the URI.
For a real implementation, you could use one of these open-source code libraries:
- Node: https://github.com/soldair/node-qrcode or https://www.npmjs.com/package/otplib
- Go: https://github.com/skip2/go-qrcode
- Python: https://pypi.org/project/PyQRCode/
- PHP: https://github.com/endroid/qr-code
Scan and add this QR with your favorite authenticator app to mimic what a user would do.
Using this URI:
otpauth://totp/Twilio:John%E2%80%99s%20Account%20Name?secret=GEZDGNBVGY3TQOJQGEZDGNBVGY3TQOJQ&issuer=Twilio&algorithm=SHA1&digits=6&period=30
Generates this QR code using qr-code-generator.com:

Scanning this QR using the Twilio Authy app generates this token:
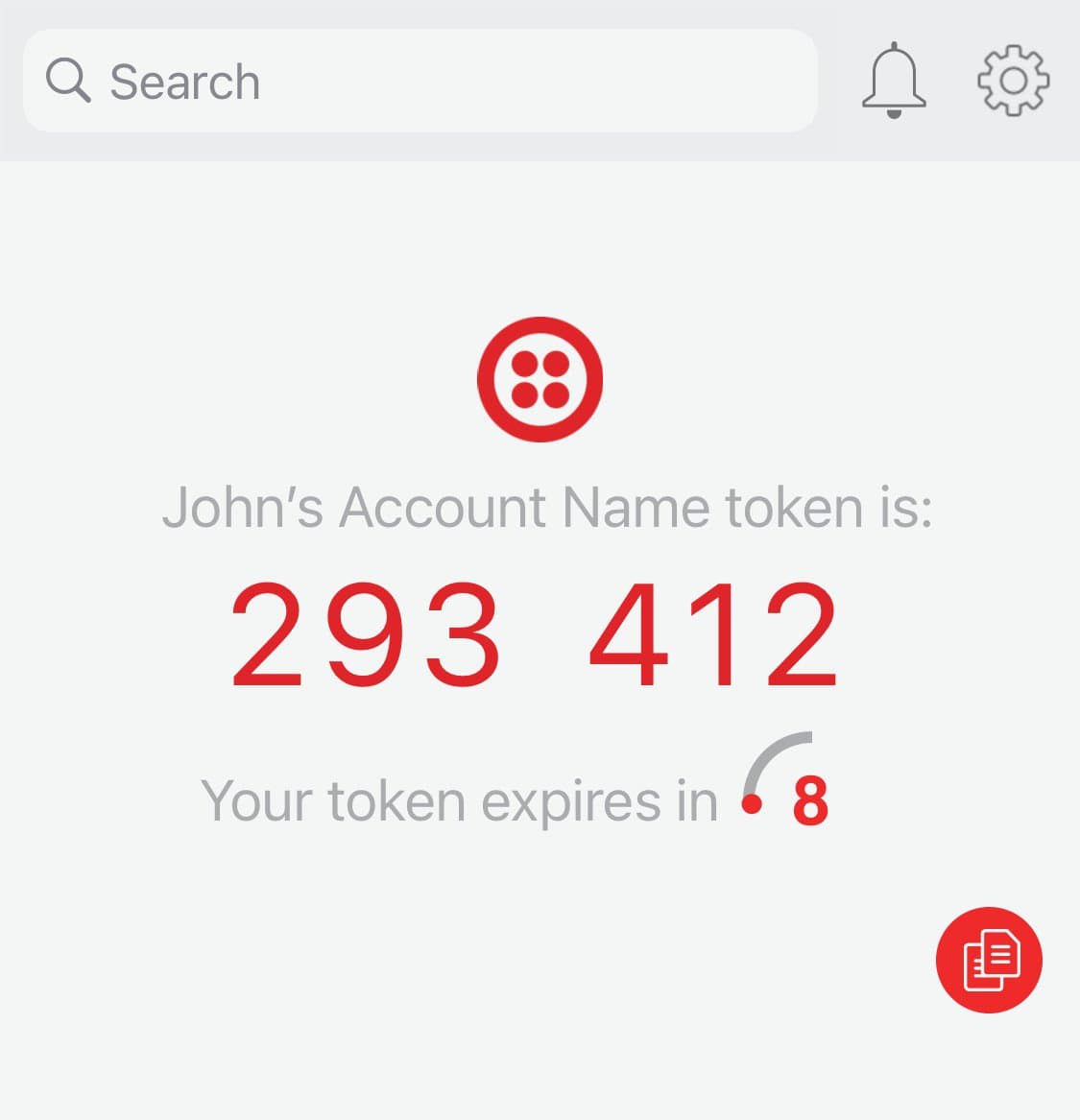
When the Factor is first created, it's in an "unverified" status. To verify the Factor, the user needs to demonstrate that they are able to generate a correct code based off of the seed.
Use the code generated by your authenticator app and type or paste the code sample for this step.
Info
Be sure to update the AuthPayload value with your latest TOTP code before sending the API request. The expiration window (Config.TimeStep) of the TOTP code defaults to 30 seconds. If the TOTP code is correct, then the Factor status will change to "verified". If it's incorrect, the Factor status will remain "unverified."
1// Download the helper library from https://www.twilio.com/docs/node/install2const twilio = require("twilio"); // Or, for ESM: import twilio from "twilio";34// Find your Account SID and Auth Token at twilio.com/console5// and set the environment variables. See http://twil.io/secure6const accountSid = process.env.TWILIO_ACCOUNT_SID;7const authToken = process.env.TWILIO_AUTH_TOKEN;8const client = twilio(accountSid, authToken);910async function updateFactor() {11const factor = await client.verify.v212.services("VAaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa")13.entities("ff483d1ff591898a9942916050d2ca3f")14.factors("YFaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa")15.update({ authPayload: "293412" });1617console.log(factor.status);18}1920updateFactor();
Response
1{2"sid": "YFaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa",3"account_sid": "ACaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa",4"service_sid": "VAaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa",5"entity_sid": "YEaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa",6"identity": "ff483d1ff591898a9942916050d2ca3f",7"date_created": "2015-07-30T20:00:00Z",8"date_updated": "2015-07-30T20:00:00Z",9"friendly_name": "friendly_name",10"status": "verified",11"factor_type": "totp",12"config": {13"alg": "sha1",14"skew": 1,15"code_length": 6,16"time_step": 3017},18"metadata": null,19"url": "https://verify.twilio.com/v2/Services/VAaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa/Entities/ff483d1ff591898a9942916050d2ca3f/Factors/YFaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa"20}
Info
The Factor SID (YFXXX..) is included in the response when you create a Factor. If you don't have the Factor SID, you can List Factors for your user's Entity, and identify the one that is factor_type = totp.
1// Download the helper library from https://www.twilio.com/docs/node/install2const twilio = require("twilio"); // Or, for ESM: import twilio from "twilio";34// Find your Account SID and Auth Token at twilio.com/console5// and set the environment variables. See http://twil.io/secure6const accountSid = process.env.TWILIO_ACCOUNT_SID;7const authToken = process.env.TWILIO_AUTH_TOKEN;8const client = twilio(accountSid, authToken);910async function listFactor() {11const factors = await client.verify.v212.services("VAaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa")13.entities("ff483d1ff591898a9942916050d2ca3f")14.factors.list({ limit: 20 });1516factors.forEach((f) => console.log(f.sid));17}1819listFactor();
Response
1{2"factors": [3{4"sid": "YFaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa",5"account_sid": "ACaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa",6"service_sid": "VAaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa",7"entity_sid": "YEaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa",8"identity": "ff483d1ff591898a9942916050d2ca3f",9"date_created": "2015-07-30T20:00:00Z",10"date_updated": "2015-07-30T20:00:00Z",11"friendly_name": "friendly_name",12"status": "unverified",13"factor_type": "totp",14"config": {15"alg": "sha1",16"skew": 1,17"code_length": 6,18"time_step": 3019},20"metadata": null,21"url": "https://verify.twilio.com/v2/Services/VAaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa/Entities/ff483d1ff591898a9942916050d2ca3f/Factors/YFaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa"22}23],24"meta": {25"page": 0,26"page_size": 50,27"first_page_url": "https://verify.twilio.com/v2/Services/VAaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa/Entities/ff483d1ff591898a9942916050d2ca3f/Factors?PageSize=50&Page=0",28"previous_page_url": null,29"url": "https://verify.twilio.com/v2/Services/VAaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa/Entities/ff483d1ff591898a9942916050d2ca3f/Factors?PageSize=50&Page=0",30"next_page_url": null,31"key": "factors"32}33}
Congratulations! You've just completed the first Verify TOTP sequence: register user and TOTP seed. The second sequence is to verify (authenticate) a user with their authenticator app, whenever they need to login to your app or perform some other sensitive action. Read on for the step-by-step instructions.
To verify a user, the user needs to read the latest code generated by their authenticator app and provide it to you. Then you need to create a Challenge and include the code as the AuthPayload. If the code is correct, then the Challenge will be created with a status of approved. Incorrect codes will result in a Challenge that is created with a status of pending, and will eventually expire. In the event of an incorrect code, you can ask the user to provide a new code and create a new Challenge to check if it's correct. Alternatively, you can update the existing Challenge with a new AuthPayload value, but this approach is probably more complicated to implement. Type or paste the code sample for this step.
1// Download the helper library from https://www.twilio.com/docs/node/install2const twilio = require("twilio"); // Or, for ESM: import twilio from "twilio";34// Find your Account SID and Auth Token at twilio.com/console5// and set the environment variables. See http://twil.io/secure6const accountSid = process.env.TWILIO_ACCOUNT_SID;7const authToken = process.env.TWILIO_AUTH_TOKEN;8const client = twilio(accountSid, authToken);910async function createChallenge() {11const challenge = await client.verify.v212.services("VAaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa")13.entities("ff483d1ff591898a9942916050d2ca3f")14.challenges.create({15authPayload: "123456",16factorSid: "YFaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa",17});1819console.log(challenge.status);20}2122createChallenge();
Response
1{2"sid": "YC02aaaaaaaaaaaaaaaaaaaaaaaaaaaaaa",3"account_sid": "ACaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa",4"service_sid": "VAaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa",5"entity_sid": "YEaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa",6"identity": "ff483d1ff591898a9942916050d2ca3f",7"factor_sid": "YFaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa",8"date_created": "2015-07-30T20:00:00Z",9"date_updated": "2015-07-30T20:00:00Z",10"date_responded": "2015-07-30T20:00:00Z",11"expiration_date": "2015-07-30T20:00:00Z",12"status": "approved",13"responded_reason": "none",14"details": {15"message": "Hi! Mr. John Doe, would you like to sign up?",16"date": "2020-07-01T12:13:14Z",17"fields": [18{19"label": "Action",20"value": "Sign up in portal"21}22]23},24"hidden_details": {25"ip": "172.168.1.234"26},27"metadata": null,28"factor_type": "totp",29"url": "https://verify.twilio.com/v2/Services/VAaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa/Entities/ff483d1ff591898a9942916050d2ca3f/Challenges/YC02aaaaaaaaaaaaaaaaaaaaaaaaaaaaaa",30"links": {31"notifications": "https://verify.twilio.com/v2/Services/VAaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa/Entities/ff483d1ff591898a9942916050d2ca3f/Challenges/YC02aaaaaaaaaaaaaaaaaaaaaaaaaaaaaa/Notifications"32}33}
Now that you've verified your first user, we'd love your feedback on your experience and whether you plan to use Verify TOTP in production. We'd be happy to discuss your plans and offer suggestions. In addition, explore adding Verify's other verification channels beyond TOTP.
Let's build something amazing.